Security awareness training is full of advice that once made sense—back when emails looked like letters, people sat at desks, and cyber attacks were basic enough to catch with a quick spellcheck.
But environments change. Threats evolve. And so do the people we’re trying to protect. It’s the nature of security training evolution.
If we continue to give the same advice without questioning its relevance, we risk overwhelming our workforce—or worse, giving them a false sense of safety.
Here are five outdated security habits many security awareness professionals have quietly stopped teaching, and the more effective behaviors we’re focusing on instead.
1. Stop hunting for typos, start spotting emotional triggers
When cyber criminals rushed their emails and couldn't spell “receive” correctly, grammar was your first line of defense. But AI-powered content tools changed everything.
Today’s phishing emails read like they were crafted by your most articulate colleague—because they often were, thanks to AI. The real danger isn’t in the spelling; it’s in how these messages make you feel.
Why we stopped: Poor grammar just isn't a reliable signal anymore. AI has cleaned up most phishing emails, and focusing on language mechanics causes people to miss subtler manipulation tactics such as:
Pretexting: where attackers research you enough to sound like they belong in your world
Authority manipulation: impersonating someone whose requests you wouldn't normally question
Reciprocity traps: doing you a small "favor" first to make their ask feel reasonable
These psychological techniques work regardless of perfect spelling.
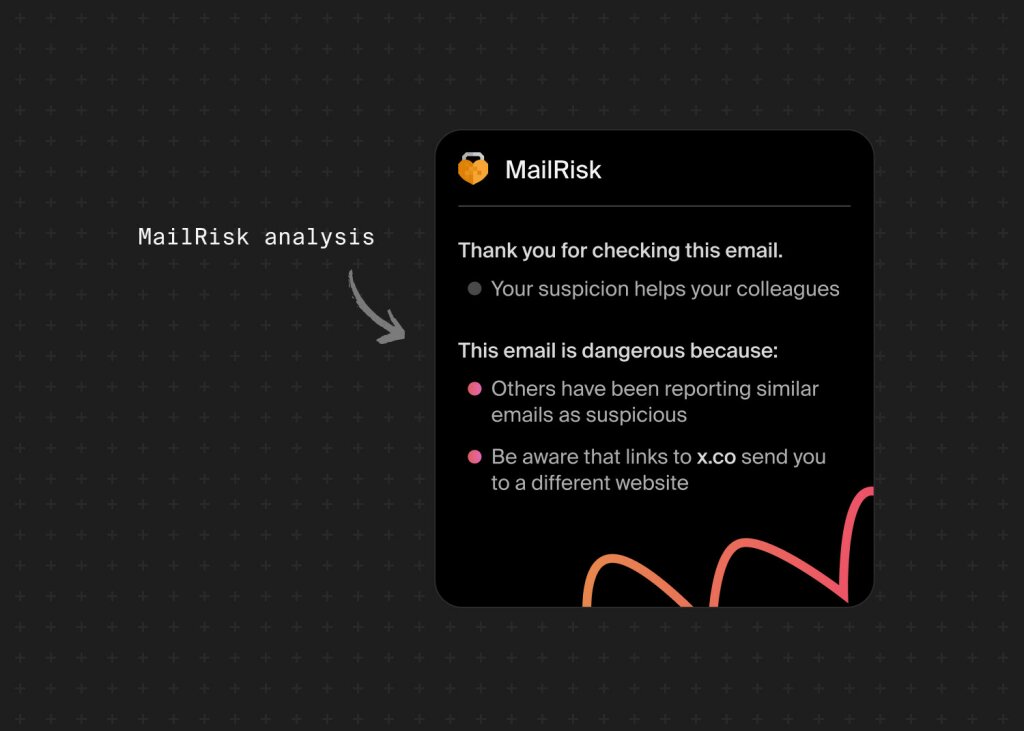
What we do instead: We help people recognize urgency, fear, and false familiarity—the emotional pressure points attackers use to get you to act without thinking.
When someone gets an email that feels pushy or creates artificial urgency, email reporting tools like MailRisk let them pause and get instant feedback on what they're seeing, helping them understand whether that uncomfortable feeling is actually their brain detecting manipulation.
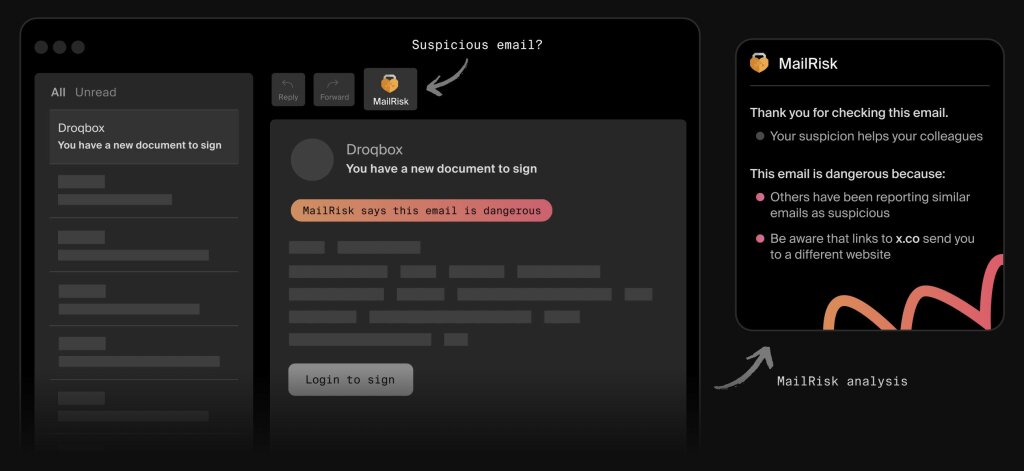
2. From hover gymnastics to simple pause-and-think
We used to teach people to hover over every link like they were defusing an explosive device. It seemed so logical—peek before you click, see where you're really going.
But then smartphones happened. And enterprise security tools that wrap every URL in multiple layers of protection and tracking codes made links even harder to decipher.
Why we stopped: Mobile browsing have made hovering impractical, and tools like Safelinks transform URLs into unreadable strings like "protection.office365.com/safelinks/url?data=..."
What used to be a simple safety check became an exercise in decoding IT infrastructure. People who couldn't master the technique—or got confusing results—often stopped being cautious altogether.
“Hovering over the link is something that I’ve started to leave out of my lessons. Especially when people started asking how to do this on a cell phone," shares one security analyst.
What we do instead: We talk about intention and context:
Does this email make sense?
Is the request typical?
Was I expecting to receive this link?
Have I seen and used this before?
These questions work whether you're on a phone, tablet, or desktop because they focus on the human elements that don't change across devices.
Instead of asking people to become URL forensics experts, we help them trust their instincts about whether a request feels normal for that relationship. A link from your bank on a Tuesday afternoon asking you to "verify your account" hits different than the same request at 2 AM on a Sunday.
Instead of teaching technical tricks, we use simulated phishing exercises that feel like real emails in an actual inbox. This lets people practice that moment of "wait, something feels off" without the stakes of accidentally clicking something dangerous.
3. Public Wi-Fi reality check: safety over abstinence
"Never use public Wi-Fi" made sense when most connections were unencrypted and VPNs required IT support to configure. But that advice stopped matching how people actually work and live.
Why we stopped:
The "never use public Wi-Fi" rule came from an era when connections were largely unencrypted and consumer VPNs didn't exist.
But today's reality is different: people work from airports, coffee shops, and co-working spaces as part of their routine. Most major apps and websites use end-to-end encryption by default, and VPNs have become as simple to use as any other mobile app.
Telling someone to avoid public Wi-Fi entirely is like telling them to never eat at restaurants—technically safer, but completely disconnected from reality.
What we do instead: We teach people to think in terms of risk levels: checking the weather on public Wi-Fi is different from logging into your bank account. Some activities are fine with basic precautions, others are worth waiting until you're on a trusted network.
The goal of cybersecurity training programs is to help people make informed choices, not try to scare them into abstinence.
Rather than just telling people what to do, our gamified e-learning platform lets them practice these decisions in scenarios that mirror their real lives—like choosing between "Free WiFi" and "Starbucks_Guest" or deciding whether that presentation deadline is worth the risk.
4. Password reality: meet people where they are
We spent years telling people not to write down passwords, as if willpower alone could help them remember dozens of unique, complex strings.
Meanwhile, they were either reusing "Password123!" everywhere or scribbling login details on sticky notes anyway.
Why we stopped: This advice assumes people can remember everything or already use a password manager. In reality, they either reuse weak passwords or write them down badly.
The "never write down passwords" rule came from an era when people had up to five online accounts and attackers needed physical access to their desks to steal written passwords.
Now the average person manages over 150 online accounts, and the most significant threats come from data breaches and credential stuffing attacks—not someone rifling through your desk drawer.
Meanwhile, telling people not to write passwords down often leads to worse behaviors: using the same simple password everywhere, or creating "systems" like adding the current month to a base password (which attackers have long since figured out).
"Full disclosure, I am now giving tips on how to write down passwords. We know they are doing it, and there are some benefits. So let's help!" admits one director of security culture.
What we do instead: We promote password managers while offering practical fallback options. People learn differently—some embrace password managers immediately, others need stepping stones.
As part of our strategy to adaptive learning in cybersecurity, we teach threat model thinking: a password written down and locked in your desk at home is infinitely safer than using identical credentials across multiple accounts.
Secure Practice's learning portal meets people where they are—with practical modules that focus on behavioral security training and human-centric security approaches.
5. Beyond the padlock: teaching real website evaluation
The little green padlock used to be a critical part of security training best practices. It whispered "trust me" in a world where SSL indicated encrypted connections that were rare and precious.
Now it's standard—even scam sites have HTTPS. Teaching people to "look for the padlock" without deeper context sets them up to trust the wrong things.
Why we stopped: In the early 2000s, getting an SSL certificate required verification and cost money, so the padlock actually indicated credibility. But services like Let's Encrypt made certificates free and automated.
By 2024, over 90% of phishing sites use SSL certificates. We accidentally taught people to equate "encrypted connection" with "trustworthy business," trusting a symbol instead of thinking critically.
What we do instead: We focus on developing judgment about digital spaces the same way you'd evaluate a physical business.
You wouldn't hand your credit card to someone selling electronics from a van, even with professional-looking business cards. The real skill is asking: Does this URL look right? Is this a site I'd trust with sensitive information?
Website evaluation isn't learned from handbooks—it's developed through practice. That's why we create collaborative environments where teams can evaluate simulated websites together, discussing what looks trustworthy without the risk of encountering actual threats.
These interactive cybersecurity exercises are part of a modern threat defense strategy, helping users build the skills they need to stay safe online at work and at home.

Security training evolution: how to avoid the noise and teach what matters
Every outdated behavior you remove creates space to focus on something more useful, realistic, and human.
Sometimes, teaching less isn't cutting corners. It's strategic and part of a security awareness change that prioritizes what really matters: behaviors that are relevant and effective against today’s threats.
That’s why Secure Practice helps you:
Automate delivery without losing the human touch
Customize learning paths by team, role, and risk level
Track progress in ways that build confidence rather than create shame
We provide privacy-focused, interactive learning experiences and human risk management tools that keep your team ahead of evolving threats while strengthening your organization's security culture from within.
Security training evolution isn't about teaching more—it's about teaching better. As one security leader puts it, "A big part of our role in securing humans is focusing on the fewest behaviors that have the greatest benefit."
Build a stronger, more informed security culture
Secure Practice offers tailored security awareness programs and scalable training solutions that focus on modern threats and smarter training strategies.