If you run a small business, chances are you already protect what matters most: your people, your customers, and your reputation.
Cybersecurity isn’t separate from that. It’s simply the same kind of care, applied to your digital tools and data.
Most business owners know security is important, but it can feel like an endless list of technical tasks: firewalls, updates, backups, passwords. Add limited time and budget, and it’s easy to postpone it until “later.”
But cybersecurity isn’t just an IT issue; it’s a business skill.
Learning how to protect your digital assets is just like learning how to balance your books or manage your team—it takes awareness, a few good habits, and the right tools. You don’t need a large security department to start making a difference.
This small business cyber security guide will help you focus on what matters most:
Understanding your biggest risks and values
Building awareness without creating fear
Protecting your data and communication
Responding confidently when something happens
Tracking progress over time
By the end, you’ll see that effective cybersecurity isn’t about perfection, but about steady progress, trust, and shared responsibility.
Small businesses are essential to digital security and equipped to lead
Most headlines talk about cybersecurity from the perspective of big corporations, mentioning billion-dollar losses, global breaches, or sophisticated state-backed attacks.
But the real foundation of digital safety lies elsewhere: in the everyday actions of small and medium-sized businesses.
You’re not “too small to matter”
Small and mid-sized businesses (SMBs) or enterprises (SMEs) make up more than 99% of companies in the EU. That means most of the internet’s daily transactions (invoices, deliveries, contracts, and customer interactions) connect directly to larger organizations through shared systems and suppliers.
That’s why even your smallest efforts matter far beyond your own company. Every email you send, every shared document, and every digital handshake adds a layer of trust that keeps the economy running.
So when you strengthen your cybersecurity, you strengthen everyone’s.
Think of the digital economy as a supply chain of trust:
When one small supplier is compromised, attackers can move upward to larger partners
When one business protects its systems and data, it prevents that chain reaction
That’s why digital resilience starts small and scales fast.
In Norway and across Europe, national preparedness exercises like Hele Norge Øver and Hele Danmark Øver are built on this principle: helping every organization, regardless of size, practice working together during an incident.

The small-business advantage
Smaller organizations face real barriers to cybersecurity: limited time, few dedicated security staff, and the assumption that “IT will take care of it.”
At the same time, smaller businesses are uniquely equipped to turn those challenges into strengths.
Smaller teams communicate faster, collaborate more easily, and adapt quickly. Those traits make it easier to build good security habits and keep awareness visible in daily work.
At Secure Practice, we see this every day; small teams that learn quickly, share knowledge freely, and take genuine pride in protecting their customers and colleagues.
This guide builds on that same idea: that security works best as a shared effort, where teamwork becomes protection and small, steady actions contribute to long-term resilience.
1. Understand what’s at stake
Every business has something worth protecting: your client list, your internal files, your reputation for reliability. Protecting these things isn’t about preparing for every possible attack. It’s about knowing where your real risks lie.
Small business security: reality check
Myth: Cybersecurity is only for big companies with IT departments.
Reality: Nearly half of all cyberattacks target small and medium-sized businesses. Attackers know smaller teams are busy and more likely to trust what looks familiar.
Most cyber incidents don’t start with hackers breaking into servers. They start with people: someone clicking a link, using a weak password, or sending a file to the wrong address.
Technology helps with preventing and addressing cyber threats, but people make the difference.
Cybersecurity for small businesses is really about creating clarity so everyone knows how to make good digital decisions. Start here:
List what you value most: customer data, invoices, intellectual property—anything hard to replace or embarrassing to lose
Map where that data lives: On laptops? In shared drives? In the cloud?
Ask what would happen if it disappeared tomorrow: this simple thought exercise turns cybersecurity from an abstract concern into a concrete business priority.
Think of it as protecting your office keys, only the doors are digital.
2. Build awareness, not anxiety
Awareness training should make people feel capable.
At Secure Practice, we’ve learned that people engage best when they understand why something matters to them.
Our gamified e-learning portal is built to start conversations instead of sending warnings, explore what led to mistakes instead of assigning blame, and adapt messages to people’s roles and experience.
The 2025 SANS report shows that real behavior change takes 3–5 years, and building a stronger security culture can take up to 10. That type of progress comes from consistency, not campaigns.
Try these simple habits:
Add short reminders to regular meetings
Keep it light and conversational. A 2-minute “security check-in” works better than a lecture. Here are some examples of what you could share:
“How to spot a fake login page” — show a quick example and what gave it away
“What to do if your laptop gets lost” — who to notify and why speed matters
“When it’s okay to share files externally” — clarify which channels are approved
Celebrate safe behavior the way you celebrate business wins
Recognition helps people see security as part of success, not a separate rulebook.
Celebrate instances of safe behavior from your colleagues, such as when:
An employee reports a suspicious email instead of ignoring it
A manager asks IT before connecting a new tool or plugin
A team updates shared documents securely rather than emailing attachments
Thank people who report suspicious activity
Close the feedback loop and build trust by following up with those who report and explaining what happened because of their action:
“Thanks for flagging that phishing email—it helped us block 15 others that came through.”
“Good catch on the login alert; it turned out to be a test, but your quick response showed the process works.”
“Appreciate you reporting the USB found in the office—IT checked it safely before disposal.”
3. Protect data and communication
Strong cybersecurity grows from small, consistent habits that keep information safe and work running smoothly.
| Focus area | Key actions | Why it matters |
|---|---|---|
| Keep access secure | Use a password manager for strong, unique passwords. Turn on multi-factor authentication (MFA). Remove access when people leave or change roles. | Basic access control stops most attacks before they start. |
| Protect your information | Store files in secure, backed-up locations. Limit who can access sensitive data. Share carefully by email or chat. | Data is part of your company’s value—handle it like an asset. |
| Stay up to date | Enable automatic updates. Keep antivirus and firewalls active. Remove unused apps or services. | Quick updates prevent downtime and close known vulnerabilities. |
| Build safe communication habits | Pause before clicking or sharing. Check sender details and payment requests. Report anything suspicious. | Awareness in everyday communication helps stop phishing and fraud. |
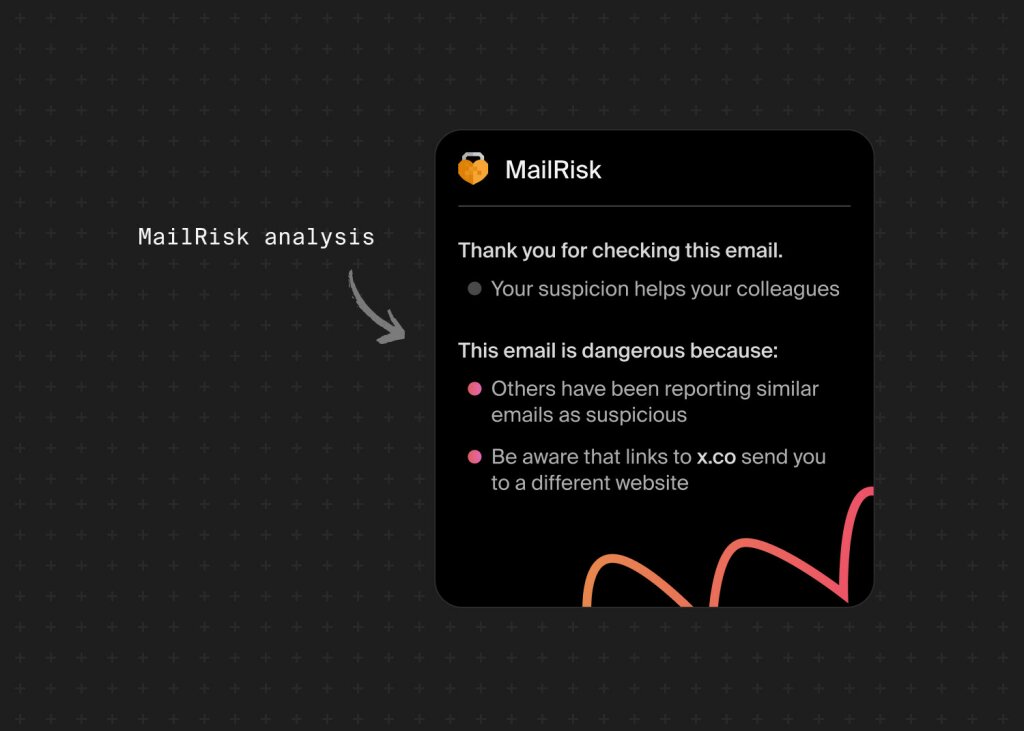
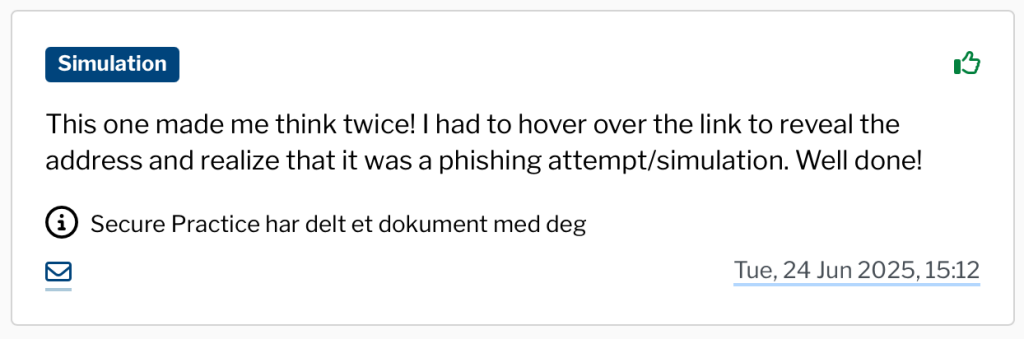
Make checking and reporting malicious or phishing emails easy. A one-click tool like MailRisk lets people flag suspicious emails safely while giving security teams useful insight.
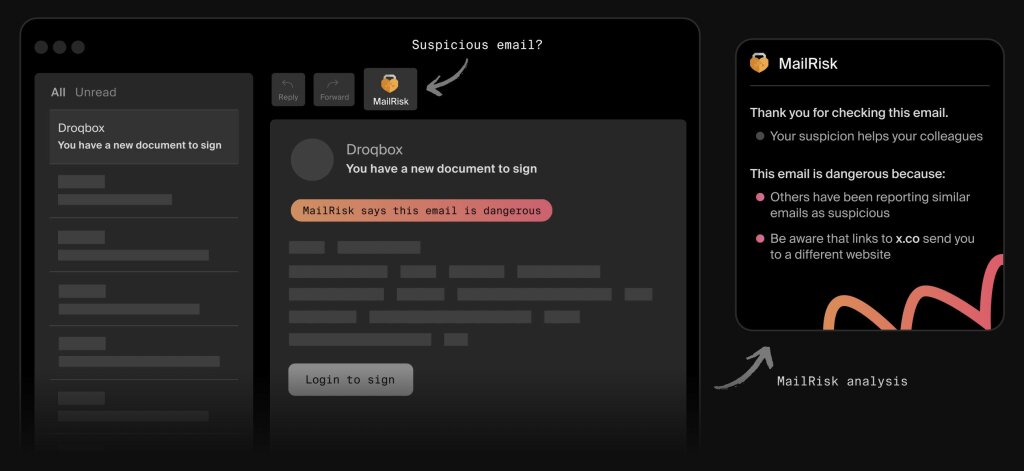
Every click becomes a chance to learn, not to assign blame.
For those in charge of security, automated filtering reduces noise and highlights real threats. Instead of reviewing tens of low-value messages, they can focus on incidents that truly matter.
Over time, this two-way process builds trust.
People start checking emails and reporting phishing attempts earlier and more often, because they know it helps
Security teams see richer insights, and phishing awareness stops being a campaign and becomes part of how people work every day
Practical tip for SMBs: Run phishing simulations regularly, but make them supportive, not punitive. The goal isn’t to measure failure, but to strengthen awareness through real-time feedback.
4. Respond and recover with confidence
Even with strong habits, incidents can happen. What matters most is how you respond when they do.
A clear plan and a calm mindset can turn a stressful event into a learning moment.
Plan before you need it
You don’t need a long crisis manual, just a clear plan that anyone can follow.
Keep a short contact list for emergencies
Store backup access details safely offline
Decide how to communicate if main systems go down
A plan that’s easy to find and understand helps everyone act quickly under pressure.
Practice crisis response before it’s real
When a cyber incident hits, panic is often the real threat. Every minute counts, yet most small businesses never rehearse incident response—what they’d do if ransomware locked their systems or if a cyber criminal tricked one of their colleagues into sending money.
Small teams rely on the hope that people will “figure it out.” But under pressure, communication breaks down and small mistakes can grow fast.
The best time to learn isn’t during a crisis—it’s before one happens.
Why traditional exercises fall short
Typical tabletop reviews or annual PowerPoint sessions don’t recreate the urgency of a real event.
They often involve only IT staff and leave little time for reflection, so lessons fade before they can take root.
Our cybersecurity exercise platform, PrepJam, turns incident rehearsal into a hands-on experience.
Instead of slides, participants receive simulated calls, emails, and alerts that evolve in real time—prompting real decisions and teamwork.
Everyone takes part: leaders, communications, and customer-facing teams alike. Even a 30-minute session can reveal gaps, spark discussion, and strengthen confidence, without heavy prep or disruption.
Practical tip for SMBs: Run a short scenario with your team and ask:
Who contacts customers if the website goes down?
How do we alert staff about a phishing wave?
These small, practical exercises help people stay calm and connected long before a real crisis ever tests them.
Restore and review
After an incident or exercise, talk openly: What worked? What didn’t? What should change next time? Learning together builds trust and readiness and helps prevent repeat mistakes.
Once recovery starts, check backups, reset access, and update affected systems. If customer data might be involved, communicate clearly and honestly.
Every incident, real or simulated, strengthens your ability to respond faster next time.
5. Measure what matters
Data is most powerful when it helps people learn, not when it’s used to assign blame.
When your team trusts that their input is used to improve the organization, they participate more and engage more deeply with security.
That’s the idea behind Human risk metrics: measuring progress without compromising privacy.
The system tracks knowledge and interest anonymously over time, showing overall trends that help you decide where to focus next.
It even lets you share results with your team so you can celebrate small wins together and make security progress visible to everyone.
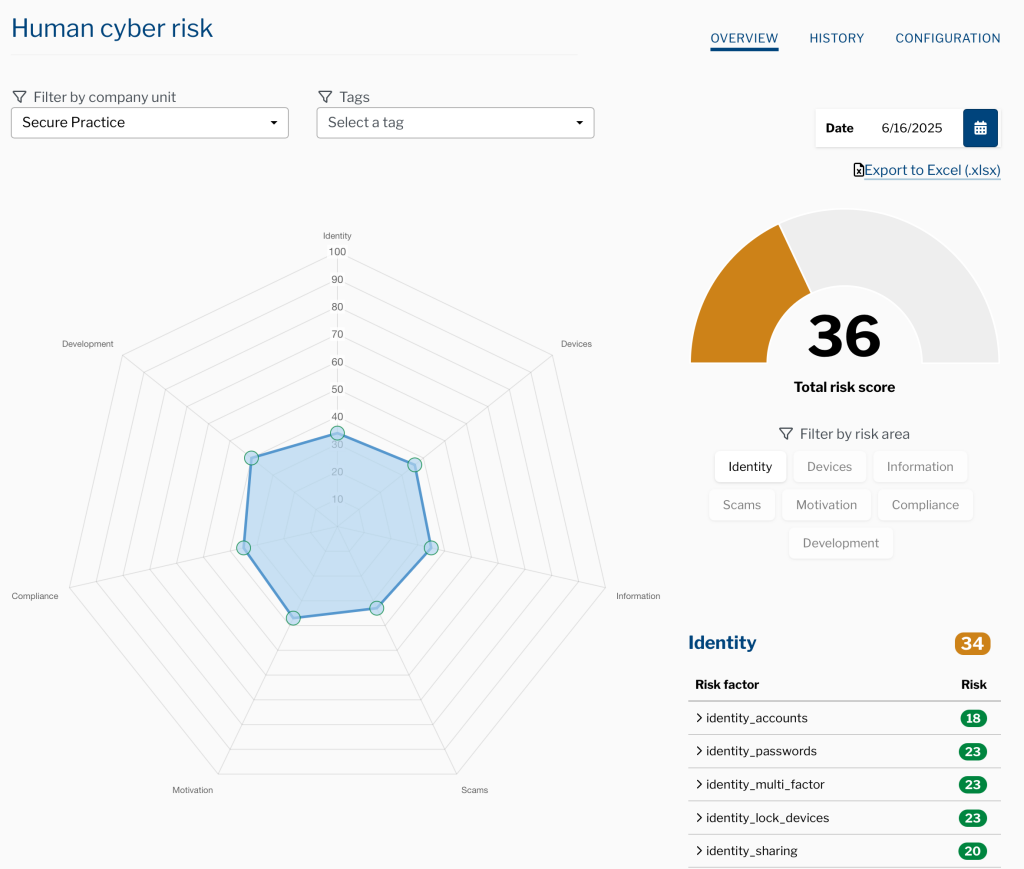
This privacy-friendly approach helps you focus their efforts where they’ll have the most impact, while building trust with employees who know their results aren’t being used against them.
Instead of reacting to mistakes, you can use data to guide learning and help teams grow their awareness in a way that fits their role and pace.
We’ve built a dashboard to help us monitor security maturity KPIs and security culture metrics are part of it. Human risk metrics help us break them down for each business area and prioritize our actions.
– Martha Eike, Security Culture, Awareness and Human Risk Management at Storebrand
Practical tip for SMBs: Modern employees, especially younger generations like Gen Z and Millennials, care deeply about privacy.
They’re less likely to engage with tools that feel invasive and more likely to support initiatives that clearly explain how their data is used.
To align your training and reporting with those expectations:
Be transparent. Tell your team what’s being measured and why before you collect data.
Share results safely. Show group trends, not individual names or scores.
Invite feedback. Ask people how the data could be more meaningful or helpful to them.
Trust grows when people feel seen, not watched, and that’s what turns data into real engagement.
The SMB Security Checklist
If you want to put everything from this guide into action, we’ve created a one-page SMB Security Checklist that brings all the key steps together.
It’s designed to help you review your security practices at a glance and share them easily across your team, without jargon or long explanations.
You can use it to:
Identify what you’re already doing well and where to improve.
Keep track of updates, training, and exercises throughout the year.
Turn awareness into consistent, practical habits.
Print it out or save it to your shared drive. Check in with your team once a quarter—even ten minutes of review can make a big difference in keeping everyone aligned.

Security is a business skill
Running a small business means wearing many hats, and “security expert” rarely feels like one of them.
The good news is that cybersecurity doesn’t have to be complex. It’s simply part of running a responsible business, protecting what you’ve built and the people who rely on it.
When you understand your risks, protect what matters most, and help your team feel confident online, you strengthen both trust and resilience—the same qualities that drive growth.
Security is good business. Every habit, every report, and every open conversation adds up to a safer workplace and a stronger digital community.
Practice today, stay calm tomorrow
Our interactive tools prepare your people for phishing, scams, and incidents—so response feels natural when it matters.
FAQs about small business cyber security
Do small businesses need cyber security?
Yes. Modern cyber crime targets businesses of all sizes. Criminals know that sensitive information, business data, and even simple login details can open the door to ransomware attacks, phishing attacks, or malicious software.
Running a small business means juggling customers, operations, finances, and now digital security. Cybercriminals know small teams have limited resources, but they also know how valuable customer data and trust are.
Everyday risks like phishing emails, weak passwords, and data leaks can affect any company. Strong habits, reliable security tools, and simple cyber essentials can keep you ahead. With awareness and practice, your people can become your strongest defense.
How much does cyber security cost for a small business?
Costs vary depending on your setup and the tools you choose. Many effective measures are affordable, such as firewalls, antivirus software or anti-malware tools, phishing simulations, and awareness training.
Small improvements in behavior and simple safeguards often provide the best return on investment.
What are the 5 C’s of cyber security?
The 5 C’s are change, compliance, continuity, cost, and coverage. They are a practical way to think about protecting sensitive data and systems.
Together, they remind business owners that security is not just about technology but also about good management and consistent attention.
What is the average cost of a cybersecurity breach at a small business?
Studies show that a single data breach can cost tens of thousands of dollars, sometimes more when you include downtime, customer loss, and recovery costs.
Taking preventive steps such as cyber security training, backups, and regular system checks is far cheaper than recovery after a ransomware attack.
Why is cyber security important for small businesses?
Small businesses often have fewer defenses than large corporations but handle the same valuable sensitive information and data. This makes them attractive targets for phishing scams, ransomware, and other attacks.
Strong security helps protect your customers, your finances, and your reputation, which are essential for long-term success.
What is the impact of cyberattacks on small businesses?
Cyberattacks can cause financial losses, disrupt operations, expose sensitive data, and damage customer trust.
Some businesses recover, but others struggle to rebuild. Preparing in advance helps minimize damage and keeps your business resilient.
What do you use to stay on top of emerging cyber threats?
Small businesses often use endpoint protection, phishing analysis, and real-time monitoring to spot issues early.
You can also follow trusted sources such as the National Cyber Security Centre (NCSC) for alerts and practical advice. Staying informed helps you act before threats escalate.
What cybersecurity measures should a small business use to protect itself?
Start with cyber essentials:
Strong passwords and multi-factor authentication
Firewalls and antivirus software
Regular updates to operating systems
Phishing awareness and reporting tools like MailRisk
Backups of business data in a secure cloud-based location
Simple steps like these reduce the risk of malicious software or data loss.
Is cyber liability insurance needed if you do not personally collect customer data?
Yes. Even if you do not store sensitive data yourself, your suppliers or systems might.
Cyber liability insurance helps cover the costs of data breaches, ransomware, or service disruptions. It adds a safety net that protects your business from unexpected expenses.
What are the best cybersecurity practices for small businesses?
Use a VPN on Wi-Fi networks, secure laptops and mobile devices, keep systems updated, and encourage staff to report phishing emails.
Running phishing simulations with MailRisk or crisis rehearsals with PrepJam helps teams build habits and confidence that last.
What are the best practices for improving cybersecurity in a small business?
Start small and focus on awareness. Share regular security tips, teach people how to spot phishing attempts, and use tools like Human risk metrics to identify where teams need more support.
Remember that not everyone in your company faces the same risks or learns in the same way. A developer might need to spot malicious code, while finance staff should be alert to fake invoices.
Keep the process positive and collaborative. The goal is to learn and grow, not to point fingers.