Imagine handing the same training manual to IT, finance, sales, and admin staff and expecting it to work for everyone. That wouldn’t make sense—so why do we still approach security training that way?
Most corporate security training assumes everyone learns the same way, relying on generic videos, quizzes, and e-learning modules that overlook differences in how different people absorb knowledge or the unique security challenges different roles face.
Learning styles, tech comfort, and job roles all shape how people take in and retain security knowledge—some need stories, others need direct hands-on experience, and many won’t care until a real-world example personally impacts them. To make training stick, we need to teach the way people actually learn—not the way security teams wish they would.
This article shows you how to adapt security training to different learning styles, make it more engaging, and fit it into daily routines with six practical examples—so your colleagues don’t just complete training but actually remember and apply it.
Why people tune out security training (and what to do instead)
Security awareness professionals are expected to train everyone—from the skeptical finance exec to the warehouse worker with no corporate email. But most training still assumes a single “ideal” learner.
Just like learning styles, security isn’t one-size-fits-all. Your constantly on-the-go sales team that’s checking emails between meetings, is more likely to skim through security tips than an office-based team with a structured workflow. Expecting both groups to engage with training in the same way is unrealistic.
Your colleagues don’t ignore security because they don’t care, they ignore it because:
The training isn’t built for them. It’s too generic and doesn’t feel relevant to their job.
The materials are overloaded with rules, jargon, and abstract risks they don’t see in their daily work.
They’re busy, and security isn’t their top priority.
They’ve been through so many trainings that it all blurs together.
What actually makes security training stick?
To make security training more effective, we need to align it with how people naturally learn. The science of learning has shown that training becomes more engaging and sticky when it taps into specific cognitive processes:
Some people need stories and real-world examples
Others learn by doing—they need hands-on exercises
Many won’t care until they experience a real threat firsthand
How to teach security the way people naturally learn
Understanding how people absorb, retain, and recall information helps create more effective security programs that adapt to different learning styles and daily workflows.
Let’s look at the science behind learning and how we can apply it to security training. Along the way, we’ll show you six practical, real-world ways to make security training engaging and effective and how Secure Practice makes it work:
1. Learning by doing: the power of active engagement
When this happens:
You send out a well-crafted phishing awareness email, and half of the responses you get are “Is this a test?” instead of colleagues actually thinking about the risk.
What’s really going on:
People stop engaging when training feels predictable. If they know it’s just another email or test, they’ll ignore it, because they’re not actively participating in their learning.
What to do instead:
Use dynamic cybersecurity exercises that adapt based on behavior and responses. This keeps the training unpredictable, helping your colleagues stay alert to real threats, not just internal tests.
For example, during Secure Practice exercises, your colleagues aren’t just told what to do; they practice making security decisions.
Think of your last security training session—everyone nodded along, but by the next day, forgot almost everything they learned. Now imagine instead a live ransomware scenario for the legal team, where colleagues work together to tackle simulated security scenarios, debating the best response in real time. Should they report a suspicious email or ignore it? What happens if they click a malicious link? Do they pay? Who do they notify?
Through these group challenges, employees learn from each other and see how their decisions impact security. That hands-on experience sticks far better than another policy reminder, turning security from a passive lesson into an active skill.

Why it works:
The science behind learning shows that people remember more when they’re actively engaged. Research like Kolb’s Experiential Learning Theory and John Hattie’s Visible Learning tells us that hands-on methods—like simulations or interactive activities—help learners retain information better than passive ones.
For example, National Training Laboratories found that retention rates jump to 75% with active exercises like simulations, while passive methods (like reading or lectures) only stick 5% of the time. In security training, that means dynamic phishing simulations work better than static emails because employees are actively practicing, not just reading.
By making training interactive, you boost both engagement and retention, giving employees the tools to spot threats in the real world when it matters most.
Personalized security: making training relevant when it matters
When this happens:
You run a security awareness webinar, and the first question from a colleague is, “Will this be recorded?”
What’s really going on
That’s code for “I don’t have time for this right now”. Time constraints and a lack of immediate relevance are major factors in disengagement.
What to do instead:
Make security feel relevant by personalizing training content based on role, risk level, and learning preferences. This is an area we are actively developing at Secure Practice, to make training feel relevant and impactful, so it becomes an essential part of the job, not just a checkbox.
For example, our simulated phishing playbook can be adapted to individual behavior. Instead of static, one-size-fits-all tests, you can analyze how employees respond to phishing attempts and adjust difficulty accordingly. Someone who regularly spots phishing might get more advanced, subtle threats, while those who struggle receive clearer, more instructive examples. This keeps training dynamic, preventing your colleagues from tuning it out while reinforcing key lessons in real time.
By making phishing training feel like real-world decision-making, people build the muscle memory to recognize and react to threats when it actually matters.

Why it works
Personalized learning is effective because it targets the unique needs and experiences of each individual, making the content more engaging and relevant. Research from the Journal of Educational Psychology shows that when training is tailored to the learner’s specific context, they are more likely to stay engaged and retain information.
When training is aligned with individual behaviors, it’s even more effective. For example, a study from The National Cyber Security Centre (NCSC) found that personalized phishing simulations reduced click rates on phishing emails by 40%. People responded better to threats that were relevant to their role, making them more prepared to act when it counts.
This means that phishing training doesn't just sit in their inbox as another item to “deal with”—it becomes something they’re actively engaged with, leading to lasting, practical learning.
3. Positive reinforcement: encouraging a growth mindset
When this happens
A team clicks on a phishing test, then complains that it was “unfair” or “tricky.”
What’s really going on:
People feel tested, not supported. If they feel that their mistakes are being punished rather than used as learning opportunities, they may become frustrated rather than motivated to improve.
What to do instead:
Focus on positive reinforcement with behavior-driven coaching. Instead of punishing mistakes, provide constructive feedback that helps teams improve.
Why it works:
People learn better when mistakes are seen as opportunities, not failures. Carol Dweck’s Growth Mindset research shows that when individuals believe they can improve, they engage more, persist through challenges, and retain information better.
For example, a 2024 study from California’s CORE School Districts found that students with a growth mindset outperformed their peers with a fixed one. In security training, constructive feedback—rather than punishment—encourages employees to stay engaged and improve over time.
By focusing on positive reinforcement, you create a culture where people feel motivated to learn from mistakes instead of fearing them.
Make your security training work in the real world
Even the best security training falls short if it doesn’t fit into colleagues’ busy workdays. For example, hosting a workshop while everyone juggles emails and report deadlines means they won’t be fully engaged—it’s just another task to squeeze in.
Try this:
Don’t rely on a single format—mix different approaches like videos, interactive modules, and simulated phishing tests to appeal to different learning styles
Use privacy-conscious learning data to tailor training without making colleagues feel watched
Recognize that some colleagues will always struggle more with security—but that doesn’t mean they’re careless
For example: instead of requiring everyone to complete a 30-minute training module, why not integrate short, relevant security tips into the tools they already use? A simple in-app reminder before colleagues share a document externally could prevent a data leak.
4. Engaging, interactive learning: making it fun and memorable
When this happens
You’ve spent weeks rolling out a phishing awareness campaign, yet some teams still click on obvious scams. You wonder, “Did they even read the training emails?” Meanwhile, IT keeps asking why security training “isn’t working.”
What’s really going on
When training is too passive, people don’t retain the information or take it seriously. They forget about risks until they experience them firsthand.
What to do instead
Offer flexible, engaging learning with microlearning modules and automated nudges that deliver bite-sized lessons when your colleagues are most likely to engage. Instead of a once-a-year box to check, this type of training makes security awareness a continuous, engaging experience that actually helps your colleagues build good habits.
Here’s how Secure Practice does it:
Bite-sized, personalized lessons keep colleagues engaged without disrupting their workflow
Automated invitations and reminders make sure everyone gets a seamless, self-paced experience
A mix of videos, quizzes, and interactive challenges keeps learning fresh and dynamic
A rewarding point system motivates people to stay involved, and earning points unlocks new content tailored to their progress
Data-driven learning adapts to what each colleague actually needs, reinforcing good security habits, not just knowledge
Why it works:
People retain more when they’re actively involved. In fact, The Cone of Experience (Dale, 1969) suggests that people retain 90% of what they actively do, compared to 10% of what they read.
Interactive training makes security lessons stick because folks aren’t just consuming information—they’re applying it. And Deci and Ryan’s Self-Determination Theory shows that interactive lessons—like gamified e-learning—keep engagement high and improve knowledge retention.
For example, Duolingo uses gamification to make language learning fun, leading to significantly higher retention rates than traditional methods. In security training, this way of learning turns awareness into an engaging challenge, making it more likely that folks will remember what they’ve learned.
By making security flexible, interactive, and habit-forming, you help colleagues stay engaged—without overwhelming them.
5. Instant feedback: turning mistakes into learning opportunities
When this happens
Colleagues forward suspicious emails to IT but don’t take any action themselves.
What’s really going on:
They see security as “someone else’s job”, not their responsibility. People don’t learn from a phishing test they failed six months ago. Without immediate feedback, it’s easy to distance oneself from the learning process.
What to do instead:
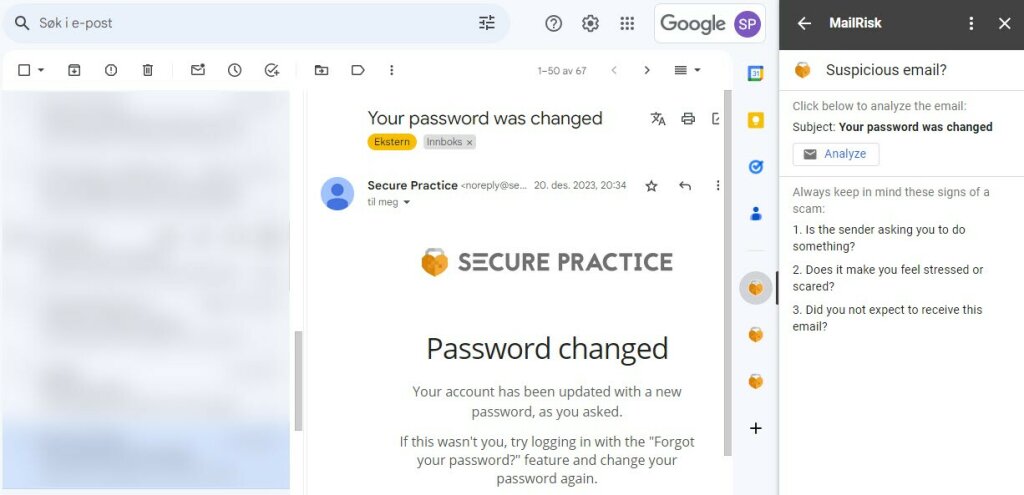
Empower colleagues with an easy-to-use phishing reporting tool directly in their inbox. This helps them learn on the spot instead of weeks later in a quarterly review.
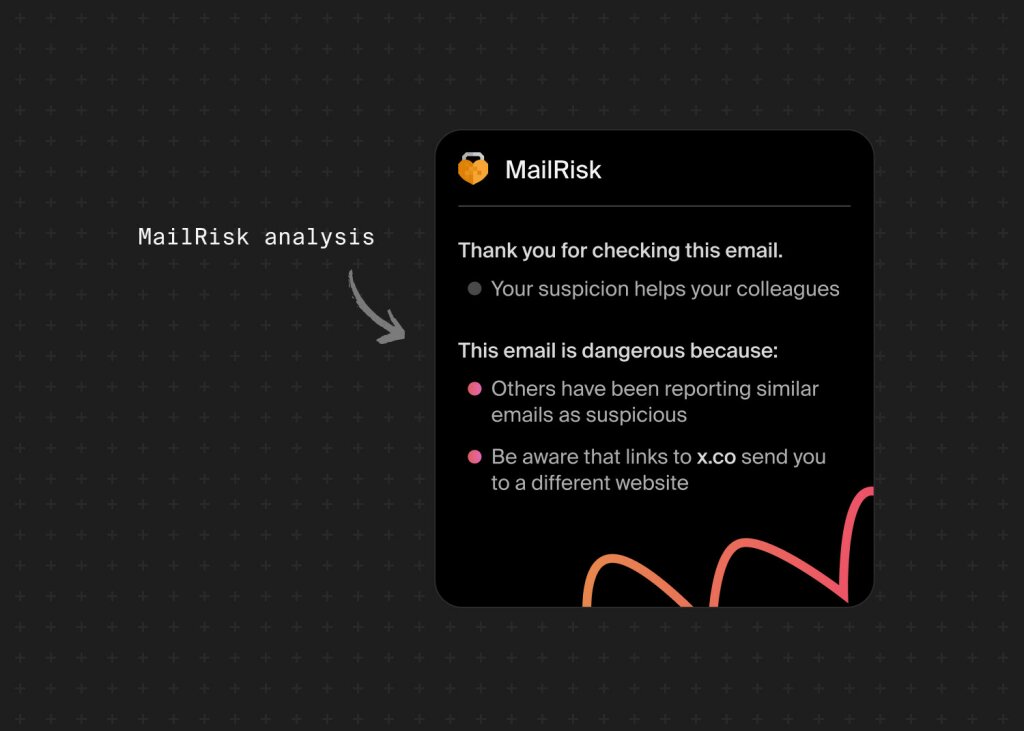
When they report a suspicious email, a tool like Mailrisk provides instant feedback explaining why the email was risky and reinforcing good habits right away. IT teams also get better data, reducing noise in phishing reports.
Why it works:
Immediate feedback builds stronger, faster instincts. B.F. Skinner’s Operant Conditioning theory shows that this type of reinforcement helps shape behavior, and research confirms that feedback works best when it’s given right away.
For example, the U.S. Armyhas developed the ER2TA Post Experience Feedback Model, which emphasizes the importance of providing feedback during the learning process to improve team performance. In cybersecurity, instant feedback on reported phishing emails helps teams learn in real time, reinforcing good security habits.
6. Human risk metrics: making security feel personal
When this happens:
A colleague in a non-technical role shrugs off security training because they believe it’s not relevant to them. “I don’t handle sensitive data, so I don’t need to worry about security,” they say.
What’s really going on:
They don’t see how their actions could be part of a bigger security issue. This mindset is common when people think they’re not the “high-risk” targets for cyberattacks. But every role in a company carries its own unique risk—and ignoring those risks can lead to vulnerabilities that threaten the entire organization.
What to do instead:
Show colleagues how their actions directly impact the company’s security posture. When they understand how individual behaviors—like clicking on phishing emails or using weak passwords—contribute to the overall security landscape, your colleagues will start to see security as more of a personal responsibility.
At Secure Practice, we track behavior patterns over time using human risk metrics without compromising privacy. This helps us create personalized follow-ups, like quick micro-courses or exercises, to make sure upskilling keeps up with your team’s evolving needs.
For example, a marketing team that thinks they’re “low risk” might be shocked to see that their team has the highest rate of phishing clicks in the company. Showing them this data allows security teams to target training more effectively—addressing specific threats, rather than delivering generic, one-size-fits-all content.

Why it works
When risks feel personal, people are more likely to take action. Research on personal relevance shows that when individuals see the personal consequences of their actions, they are more likely to change their behavior.
For example, the American Psychological Association found that people were more likely to adopt healthier habits when they could see the personal health risks tied to their choices. When they were reminded of the consequences, they understood the need for change and acted accordingly.
Human risk metrics are a powerful way to bridge the gap between general security awareness and individual action. By personalizing the learning experience and giving people insights into their vulnerabilities, you help them connect the dots and take their security responsibilities seriously.
Cybersecurity is a skill, not just a policy
You wouldn’t expect to become a great public speaker by watching one lecture. To master it, you need practice, feedback, and real-world application. The same goes for security awareness training.
The right approach helps your colleagues:
Feel more confident spotting and responding to threats
Develop habits that last beyond a single training session
Stop seeing security as a “task” and start seeing it as part of their job
When you integrate dynamic exercises, instant feedback, and role-specific training into your security program, you’ll see real engagement. Take a step today: try one of our practical, hands-on training recommendations. You’ll quickly see how it transforms security from a checkbox into a valuable skill your colleagues use every day.
Security training that works with people, not against them
Want security training that actually works? Discover how Secure Practice helps teams learn, adapt, and build real cyber resilience—in a way that makes sense for them.