This template is designed to help you build a clear, data-backed case for investing in security awareness. It guides you through identifying productivity drains, missed opportunities, and measurable risk reduction, so you can connect your initiative to the outcomes your leadership team cares about.
You’ll also find helpful tips, real-world benchmarks, and smart ways to frame the impact of training in terms of revenue protection, cost savings, and operational efficiency. Whether you’re starting from scratch or refining an existing case, this template will help you speak the language of decision-makers, to make the process easier—and your case even stronger.
How to make the most of this template
The goal of this template isn’t to fill in every blank. Instead, use each section to focus on building a compelling proposal that speaks directly to your leadership team.
Start by gathering specific, credible data. Numbers grounded in real incidents and business outcomes carry more weight than vague estimates. The more clearly you can show the current impact of poor security awareness—and the potential upside of doing better—the stronger your case will be.
Where to find relevant data
IT and security teams can share metrics on incidents, response times, and ongoing support burdens. Your help desk system is a great place to find this.
Sales and business development may have examples where stronger security practices could’ve helped close deals or meet client expectations.
Finance can help you translate delays, risks, or inefficiencies into actual costs—and ROI potential.
HR or L&D can provide context on how training is currently delivered and how engaged employees really are.
Focus on what matters most
You don’t need to complete every section. Dive deep into your top three security challenges—the ones costing your business the most time, money, or opportunity.
A business case that’s sharp, relevant, and backed by real numbers will always outshine one that tries to cover everything with guesses. Use this template as a guide to tell a story that matters to your decision-makers.
Security Awareness Training: Business Case Template
Executive summary
This section provides a brief, compelling overview that summarizes the entire business case. Highlight the key problem, solution, and expected outcome.
Our organization faces increasing cybersecurity threats targeting our most vulnerable asset—our people. This business case proposes a strategic investment in security awareness training to help reduce risk, increase resilience, and meet rising client expectations.
By investing $[X] per year, we can:
Cut down on productivity losses tied to avoidable security incidents
Strengthen our position in competitive bids by meeting client security standards
Avoid the high cost of breaches—something [X]% of similar organizations experience
Even one prevented incident could cover the cost of the program. More than that, it positions us for smarter growth in markets where security is no longer optional—it’s expected.
1. Current vulnerability assessment
Most security discussions focus on future threats, but your organization is likely already paying a "security tax" in hidden productivity drains and missed opportunities. This section reveals the current costs of inadequate security awareness—costs that are already impacting your bottom line but rarely appear as line items in financial reports.
What to consider:
Beyond help desk tickets, what other security-related interruptions impact your team's productivity?
How much time does your executive team spend addressing security concerns instead of strategic initiatives?
What customer or partner requirements related to security has your organization struggled to meet?
Hidden productivity costs
Our lack of security awareness is having a real, ongoing impact on our performance. These costs are not always captured in our financial reports, but they are still affecting productivity across the business:
IT staff currently spends [____] hours monthly cleaning up preventable security issues
Our help desk logs show [____] tickets monthly related to security problems
Employees spend approximately [____] minutes daily dealing with suspicious emails and security concerns
Business obstacles we face
Security vulnerabilities are also holding us back from pursuing critical opportunities:
[____] potential clients in the last year asked about our security awareness program
We've been excluded from [____] bidding opportunities that required security training documentation
Our current process lacks formal security awareness documentation required by many clients
Additional challenges: [____]
2. Industry risk context
Industry-specific data transforms your business case from theoretical to concrete. Decision-makers respond to benchmarks relevant to their specific sector because they provide context for how peers are handling similar risks. This section establishes that security awareness isn't just a best practice—it's becoming a standard expectation in your industry.
What to consider:
How does your security awareness maturity compare to industry peers?
What recent security incidents in your industry have made headlines, and how vulnerable would your organization be to similar attacks?
How are regulatory requirements evolving in your industry, and what role does employee training play in compliance?
Threat landscape
Understanding the industry risk gives us context for why action is needed now:
The average cost of a data breach in our industry is $[____]
For example: Healthcare: $9.77M / Financial Services: $6.08M / Manufacturing: $5.56M / Technology: $5.45M / Global Average: $4.88M (source)[____]% of organizations in our industry have been significantly impacted by a breach
Industry averages revolve around 70% depending on sector (source)[____]% of malware is delivered via email
Industry average: 94% (source)
Human factor in security
In our industry, breaches caused by human mistakes are common. Here’s what we’re up against:
[____]% of breaches are linked to human error
Industry averages revolve around 60% depending on sector (source)The average time to identify and contain a breach is [____] days
Industry averages revolve around 194 days to identify, 64 days to contain. (source)
Need more human risk context?
Secure Practice’s human risk metrics dashboard helps you spot patterns, track progress, and actually see where awareness is making a difference in your organization.
3. Business opportunity potential
Yes, preventing breaches matters. But what really gets executive attention? Opportunities to drive revenue. This section helps you reframe security awareness as a business enabler, not just a necessary cost. By showing how stronger security practices support deal-making, customer trust, and market access, you can position training as a smart investment—one that pays off in both protection and potential.
What to consider:
Which clients or partners have specifically asked about your security practices in the past year?
What new markets or opportunities could open up with improved security credentials?
How might improved security awareness impact your competitive positioning?
Client requirements
Security-conscious clients are increasingly placing greater importance on robust security practices:
[____] of our current clients now require security attestations for continued business
[____] of our proposals faced security questionnaires in the past six months
We estimate $[____] in potential new business from security-conscious clients
Operational benefits
The value of security awareness extends beyond revenue generation. By reducing incidents, we can benefit from operational efficiencies that support long-term growth:
Expected reduction in help desk ticket volume: [____]%
Expected monthly IT support time saved: [____] hours
Additional operational benefits: [____]
4. Proposed solution
The approach you recommend should speak directly to the risks and opportunities you've already uncovered. This isn’t about rolling out generic training—it’s about choosing the right solution for your organization’s specific challenges. When your proposal clearly ties back to the business needs you’ve outlined, it tells a cohesive story and makes your case a whole lot harder to ignore.
Each of these components is built to slot into your existing tools and routines, reducing disruption, increasing adoption, and delivering results fast.
What to consider:
Which format best fits your teams’ workflows and learning preferences?
Have previous training efforts been too passive, too generic, or poorly adopted?
How will we track progress in a way that reflects real behavior change—not just course completions?
Training approach
Based on the specific risks and opportunities we’ve identified, we recommend a training approach that’s tailored to our culture, past experiences, and what success looks like for us.
We’re not just looking to increase awareness. We’re aiming to build a confident, capable workforce that can recognize threats and respond effectively—without slowing the business down.
We suggest a multi-layered program designed to engage different learning styles and operational realities:
1. Interactive cybersecurity exercises
Real scenarios. Real decisions. Real collaboration.
These hands-on simulations turn awareness into action by letting teams practice high-pressure decisions together:
“Should we pay the ransom?”: a guided ransomware simulation that builds shared understanding around risk trade-offs
Team-based scenarios: simulate phishing, credential theft, and data loss situations—then walk through decisions together
Collaborative learning: reinforce teamwork and spark the kinds of conversations that build long-term vigilance
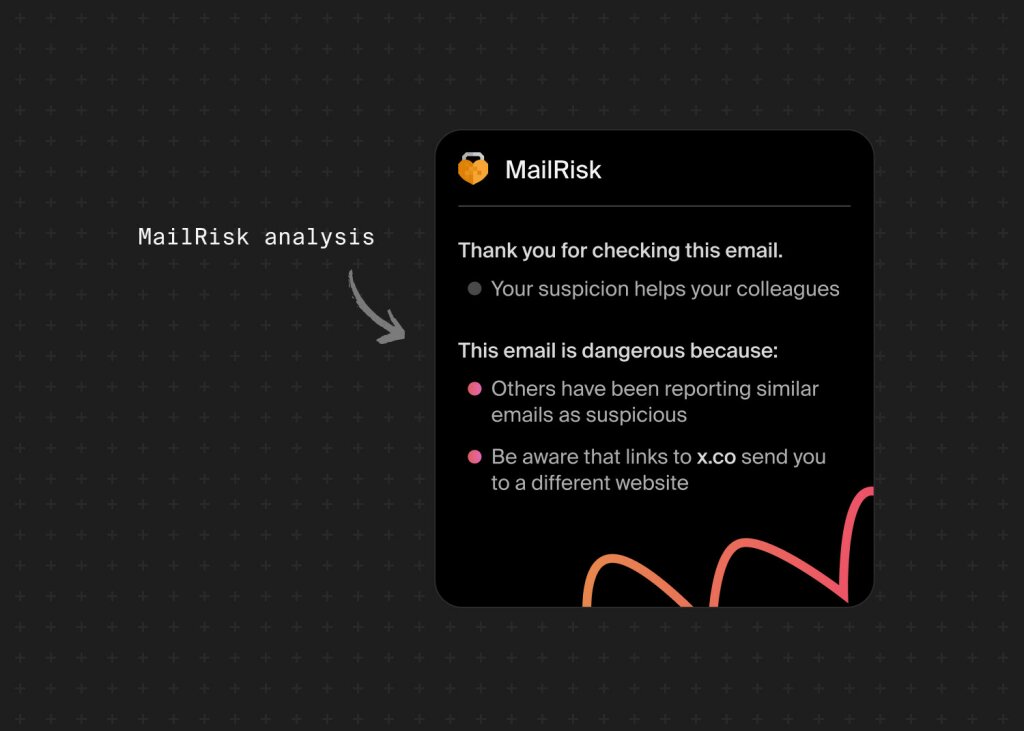
2. Email reporting and feedback tool
An integrated tool like MailRisk makes reporting suspicious emails simple and effective. This creates teachable moments exactly when they matter—at the point of action.
One-click reporting right inside the inbox
Instant, personalized feedback helps reinforce positive behaviors
Dashboard insights show where your risk hotspots and champions are
3. Gamified e-learning
A gamified approach to security awareness makes learning feel active and rewarding:
Customizable learning paths for different departments and risk levels
Leaderboards and achievements keep teams motivated
Interactive challenges simulate day-to-day security decisions in a safe space
4. Simulated phishing training
Phishing campaigns that do more than test. It’s a continuous learning loop—adaptive, behavior-driven, and always relevant.
Templates that mirror real threats and your organization’s environment
Point-of-click training turns mistakes into learning
Behavior-driven follow-ups help target the right content to the right people
Adaptive campaigns increase in difficulty as your team gets sharper
Implementation approach
A thoughtful rollout plan helps set your initiative up for success. Use this section to outline how you plan to introduce the program across your organization in a way that matches your culture, capacity, and urgency. Think about timelines, internal champions, and any support you’ll need from leadership or IT. If you're introducing new tools or processes, outline how you'll train staff and maintain momentum.
What to consider:
Phased: start with one department or region, learn what works, then expand. This approach is great if you're looking to pilot the program before scaling up.
Immediate company-wide: ideal for organizations that want to move quickly—especially after a recent incident or when leadership buy-in is already strong.
Department-by-department: focused rollouts allow each team to onboard at the right pace. This works well if departments have different needs, risks, or schedules.
We plan to introduce the program in a way that aligns with our company’s culture, available capacity, and the level of urgency we’re facing—so it’s both practical and impactful from day one:
Approach type: [Phased / Immediate company-wide / Department-by-department]
Initial rollout date: [____]
Timeline for full implementation: [____]
Department/team to start with: [____]
IT/tech support requirements: [____]
Tools or processes introduced: [____]
Training for staff: [____]
Ongoing maintenance and support: [____]
5. Investment and return
Cost is often the most significant hurdle when proposing security awareness training. But in this section, we’ll demonstrate how security awareness isn’t just a cost—it’s a smart investment with clear, measurable returns.
Required resources
What we need to get the security awareness program off the ground:
Cost per employee annually: $[____]
Number of employees: [____]
Total annual program cost: $[____]
Administration time per month (hours): [____]
Expected benefits
The benefits of a security awareness program go well beyond just preventing breaches:
Number of client contracts to be secured: [____]
Help desk ticket reduction: [____]%
Estimated annual value saved or gained: $[____]
ROI calculation
We expect the program to deliver measurable ROI that makes the investment worthwhile:
ROI percentage: [____]%
Estimated break-even time: [____] months
6. Decision request
Your business case should close with a clear path forward. This is where you turn insights into action, providing decision-makers with a straightforward ask and a roadmap to success. By setting these clear expectations, you make it easy for leadership to approve and support this initiative.
Approval request
To move forward, we need the following:
Annual budget approval of $[____]
Program rollout to begin by [date: ____]
Support for mandatory participation from all departments, ensuring full engagement
Final approval requested by: [date: ____]
Measurement plan
To ensure transparency and track success, we’ll use the following metrics:
Monthly training completion rates: tracking participation and course progress
Security-related help desk tickets: monitoring incident frequency and severity
Bid success rate on security-conscious proposals: measuring new opportunities unlocked by improved security practices
Additional metrics: [____]
How to strategically present your business case
Schedule the right conversation
Don’t leave your business case to an email. Request a dedicated meeting with key decision-makers, ensuring security awareness takes center stage. Be prepared with a brief, impactful presentation that highlights the most compelling parts of your case.
Know your audience
Tailor your message to the priorities of different stakeholders:
CFOs and financial decision-makers: focus on ROI, cost avoidance, and quantifiable benefits
CIOs and technical leaders: highlight reduced IT burden and improved security metrics
CEOs and business leaders: emphasize how security awareness enhances competitive advantage and unlocks new business opportunities
Timing matters
Present your business case when it's most likely to receive attention. For example, during annual budget planning or following a publicized breach in your industry. Avoid times when competing priorities may overshadow security concerns.
Prepare for objections
Be ready for common pushback, such as "we’ve never had a serious breach" or "we can’t afford the downtime." Have responses ready that acknowledge concerns while reinforcing the business value and long-term cost savings you’ve identified.
Keep it concise
Executives appreciate brevity. Create an executive summary that captures your key points in under two minutes, with the full business case available for those who want to dive deeper.
Next steps after completing your business case
1. Start small if necessary. If securing full budget approval is tough, suggest a pilot program with a high-visibility team or department. Use these results to build momentum and support for broader implementation.
2. Leverage external events. Monitor industry security incidents or breaches at competitors. These can serve as timely opportunities to revisit your business case and increase urgency.
3. Measure and report. Once any component of your training program is in place, track the key metrics outlined in your business case. Documenting results will build credibility, making future requests easier.
Need more guidance?
Secure Practice's security consultants can help you refine your business case, identify the most relevant metrics for your organization, or present to your leadership team. Get in touch to schedule a free consultation and let’s discuss your unique challenges.