Simulated phishing: How to design a suitable scam
How do you prepare the most effective phishing email to serve the goal of your exercise? In the third part of this series on simulated phishing, we describe various approaches to designing phishing content.

How to succeed with security behavior change
To stay safe online, people need to care more about the security decisions they face every day. But unless the obvious gains obviously exceed the required effort, change is often avoided. Luckily, behavior change in general has been subject to a lot of research, and here are some takeaways for information security professionals.

Simulated phishing: Communications strategy
How do you prepare an organization for you to try and trick them? In the second part of this series on simulated phishing, we provide the outline for a communications plan.

Simulated phishing: Goals and methodology
Is it okay to trick your own colleagues? With simulated phishing, this is precisely what we do, when sending employees fake emails to increase their cyber awareness.

Feeling the difference between human error and secure behavior
What do emotions and empathy have to do with digital security? Can job satisfaction increase password quality? See the talk on what scientific research on these matters.

How to find email headers in Outlook
Have you ever received an email and wondered if it could be dangerous? It is definitely a good idea to report the suspicious email to IT, but the usefulness of your reporting increases if you are able to analyze the email headers.
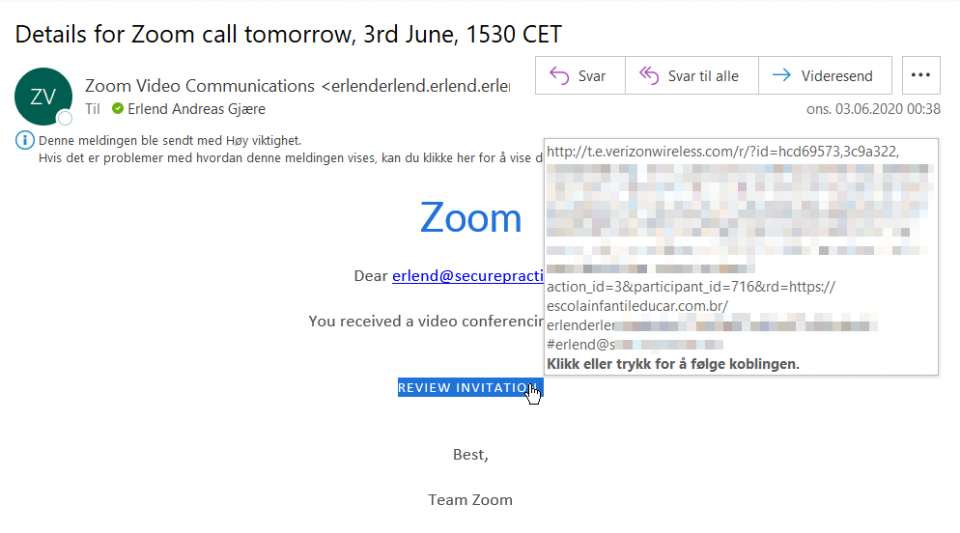
Detection evasion through abused redirect
Does your website allow the forwarding of end-users to URLs provided as a user-provided URL parameter? If so, it may potentially be abused in phishing campaigns, along with your web domain reputation.
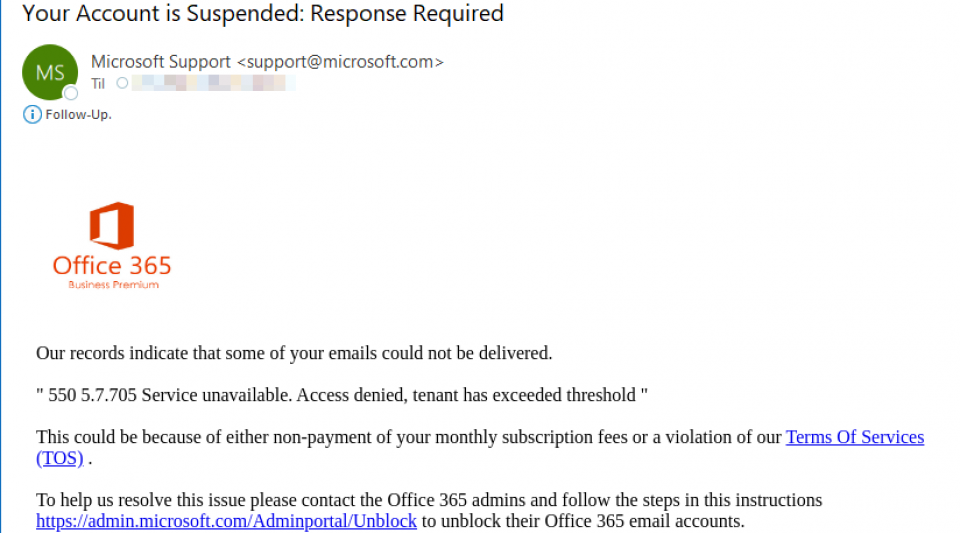
SPF shortcomings with Return-Path in spoofed emails
Email was never designed to be safe, but protocol additions like SPF have improved our ability to detect spoofed senders. We have discovered a trend in forging the Return-Path header, which SPF does not deal with on its own.

Phishing with Azure AD B2B Collaboration
The email has invites@microsoft.com as sender, and every technical investigation (both SPF, DKIM and DMARC) shows that the email itself has indeed been sent from Microsoft.

Secure software with OWASP ASVS
Are you working on security requirements in software development, test or procurement? There is no need to re-invent the wheel. See the talk on how OWASP Application Security Verification Standard (ASVS) can help.

Experiences with simulated phishing
Are you assessing whether simulated phishing may be a good thing to do in your company? See this video for useful steps and input to prepare and launch your own internal phishing campaign.
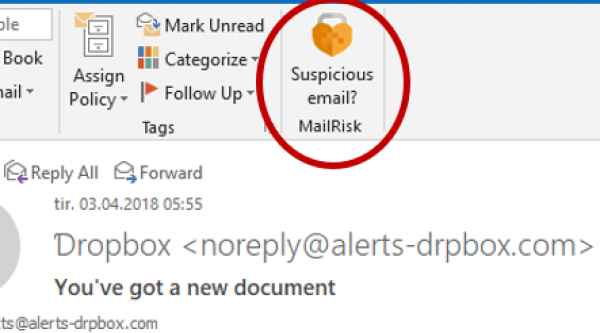
Onboarding info for new MailRisk users
When the MailRisk button suddenly appears in the Outlook app for your colleagues, it is important to tell them what this shiny new button is all about. Here is a suggested way to go forward.

MailRisk wins best new security product award
It was a great pleasure for us to receive the Outstanding Security Performance Award (OSPA) at the Norwegian Business and Industry Security Council (NSR) security conference.
Ready to get started?
We have written a guide for you to get started with human-centered security. Access our free resource now, and learn:
- How to nurture drivers for employee engagement
- How to avoid common obstacles for reporting
- Practical examples and steps to get started

